2019深思杯
上下左右
flag.txt:
1 | DDDDDDDDDRRRRRRDDDDDDDDDDDDDDDDLLLDDDDDDDDDDDLLRRRRLLDDDDDDDDDDDDDDDDDDDDDDDDUUUUUUUUUUUUUUUUUUUURRRRRRRUUUUUUUUUUUUUUUDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDUUUUUUUUUUUUUUUUUUUURRRRRRRRUUUUUUUUUUULLLLLRRRRRRLDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDLLLLUUUUUUUUUUUUUURRRRUUUUURRRRRUUUUUUUUUUURRRRRDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDLLLLLUUUUUUUUUUUUUUUUUUUDDDDDDDDDDDDDDDDDDDRRRRRRLDDDDDDDDDDDDDLLLLLLLRRRRRRRRLUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUURRRRRUUUUUUUUUUUUUUUUURRLLDDDDDDDDDDDDDDDDDDDDDDLLDDDDRRDDDDDDDDDDDDDDDDDDDDDDDRRLLUUUUUUUUUUUUUUUUUUUUUUULLUUUURRUUUUURRRRRRRRUUUUUUUUUUULLLLLRRRRRRLDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDLLLLUUUUUUUUUUUUUURRRRUUUUURRRRDDDDDDDDDDDDDDDDDDDDDDRRRRRLLLLLUUUUUUUUUUUUUUUUUUUUUURRRRRUUUUUUUUUUUUUUUULLLLLRRRRRDDDDDDDDDDDDDDDDRRRUUUUUUUUUUUUUUUURRRRLLLLDDDDDDDDDDDDDDDDRRRRDDDDDDDDDDDDDDDDDDDDDDLLLLRRRRUUUUUUUUUUUUUUUUUUUUUURRRRRUUUUUUUUUUUUUUUURRRRRDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDLLLLLUUUUUUUUUUUUUUUUUUUUUURRRRRRRRRRRRUUUUUUUUUUUUUUUULLLLLRRRRRDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDLLLLLRRRRRUUUUUUUUUUUUUUUUUUUUUURRRRRRRUUUUUUUUUUUUUUUULLLLLRRRRRDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDLLLLLRRRRRUUUUUUUUUUUUUUUUUUUUUURRUUUUUUUUUUUUUUUURRRRRDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDLLLLLUUUUUUUUUUUUUUUUUUUUUURRRRRRRRRRUUUUUUUUUUUUUUUUUUUUULLLRRRDDDDDDDDDDDDDDDDDDDDDDDDRRDDDDLLDDDDDDDDDDDDDDDDDDDDLLL |
1 | # encoding: utf-8 |
压缩包的秘密
直接打开压缩包
查看16进制:
1 | 0000000 504b 0304 1400 0900 0800 d772 554f 9f43 |
发现两个字节位置不对,写脚本交换两字节位置,恢复压缩包
1 | S='4B50040300140009000872D74F55439F46CE0034000000260000000800006C666761742E7478C21C1AF9380F7F03C962F53BED1B5385CA595270F34D7C254B8FC92A76A115C99800EFAA55BF064FF3E37E7CF843E767B1DB813A4B500807439F46CE00340000002600004B500201001F00140009000872D74F55439F46CE00340000002600000008002400000000000000200000000000006C666761742E7478000A0020000000000001001844B9F4F387D701D53904C216855101D53904C216855101D54B5006050000000000010001005A0000006A000000800D09200A20200D20200A0A0D09200D20200A0A0D2009202009200A0D20200A0D20200D20090A202020200D09200A20200D20200A0D09200A20090D20200A09200D20090A202020200D09200A09090D20200A09090A0D20090D20090A202020200D09200A20200A0D20090D20090A0D20200A0D20200A20200A0D200920090A0D47646C686D6374555861744D47617346695A77313264745132636C686E62704E' |
解压压缩包发现里面有一个加密的flag.txt
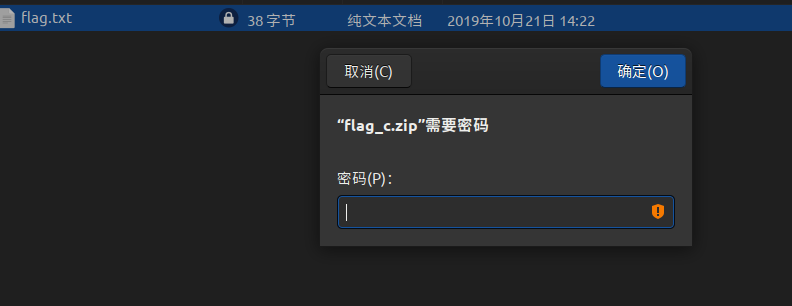
在查看16进制,发现底部有base64编码,解码后提示一半的密码,shensi,不过这一半的密码… 是后6位密码,并不是前6位(巨坑!),接下来可以掩码爆破,也可以猜测出来…密码:sdniscshensi
flag{5b3fcbb6920490bf4ab156df51c0976c}
我和我的祖国
音频分析发现信息隐藏在最后
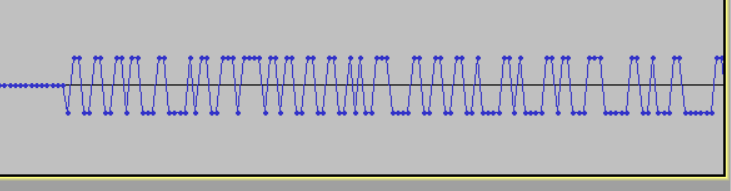
下面的是0,上面是1
查看16进制:

F0D8 --> 1
1027 --> 0
解题脚本:
1 | # encoding= utf-8 |
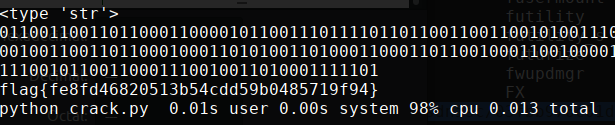
Forensic-日志分析
1 | 192.168.117.1 - - [08/Oct/2019:14:02:12 +0800] "GET /admin/?id=1%27%20AND%20ORD%28MID%28%28SELECT%20IFNULL%28CAST%28flag%20AS%20CHAR%29%2C0x20%29%20FROM%20dvwa.flag%20ORDER%20BY%20flag%20LIMIT%200%2C1%29%2C1%2C1%29%29%3E96%20AND%20%27ZeOx%27%3D%27ZeOx HTTP/1.1" 200 209 "-" "sqlmap/1.3.10.7#dev (http://sqlmap.org)" |
二分注入
简单的密码
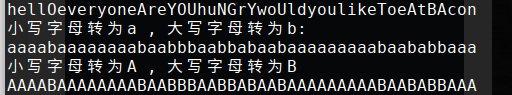
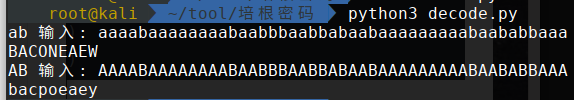
hellO,everyone Are YOU huNGrY woUld you like To eAt BAcon
培根密码
有两种解密模式:
- 小写字母转为a , 大写字母转为b
- 小写字母转为A , 大写字母转为B
1 | #encoding=utf-8 |
1 | letters1 = [ |
1 | import re |
流量分析
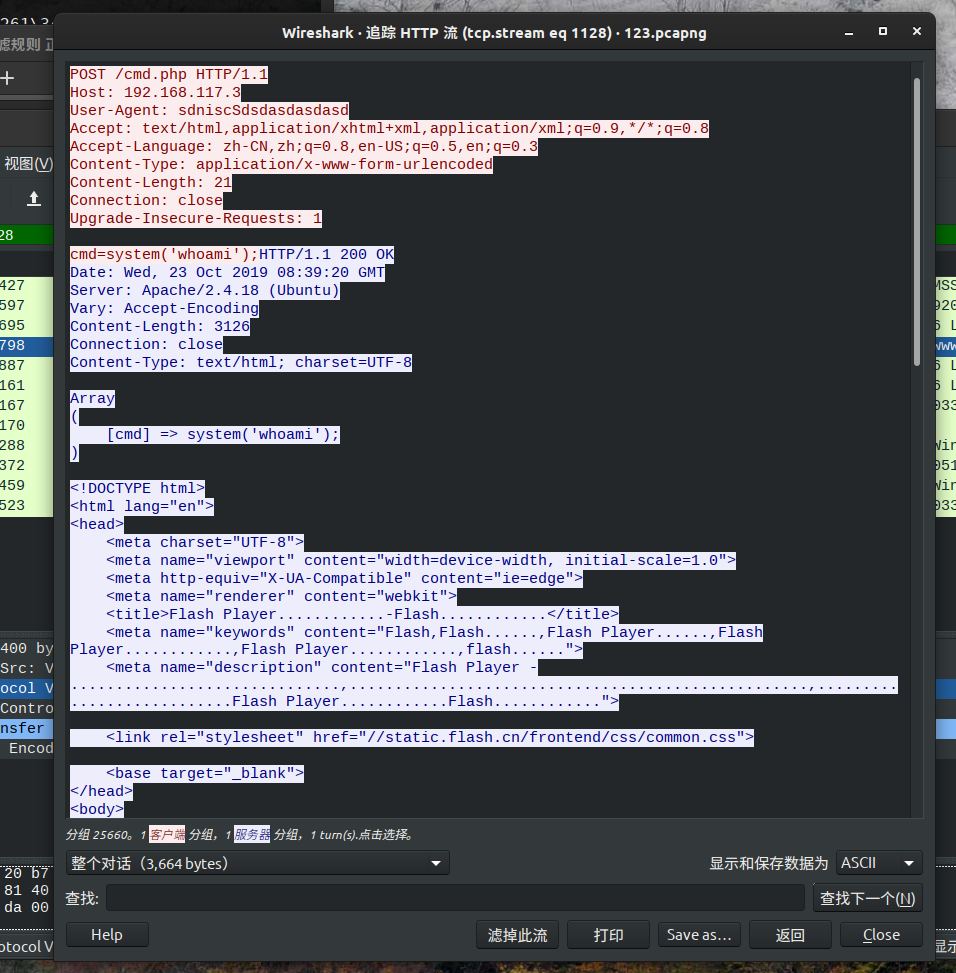
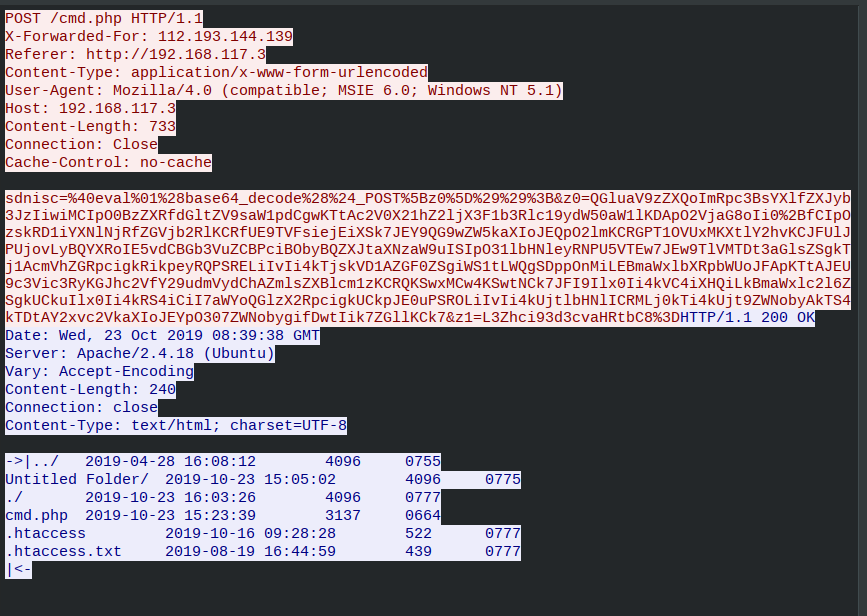
查看一下http流,发现非常多的http请求,看得出是在进行目录爆破,那就查看哪个目录爆破成功,爆破成功返回200,但是流太多,所以先搜了一下可疑内容http contains "cmd" 然后打开搜寻出现的流量,过滤掉一些无用的流量后,在tcp.stream eq 76发现了一个请求成功的php: cmd.php,直接过滤掉请求失败的http contains "200"在tcp.stream eq 1128看到了命令执行过程:
tcp.stream eq 1354
unicode解码看一下:
1 | from urllib import parse |
将z0的内容解码并排版:
1 | @ini_set("display_errors","0"); |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来源 Rick!
评论


