极客大挑战2019
EasySQL
尝试了一下空格,or,'等发现没有过滤然后试了个万能密码 1' or '1…就出来了???。。。
可能是buuoj环境搭建错了吧。。
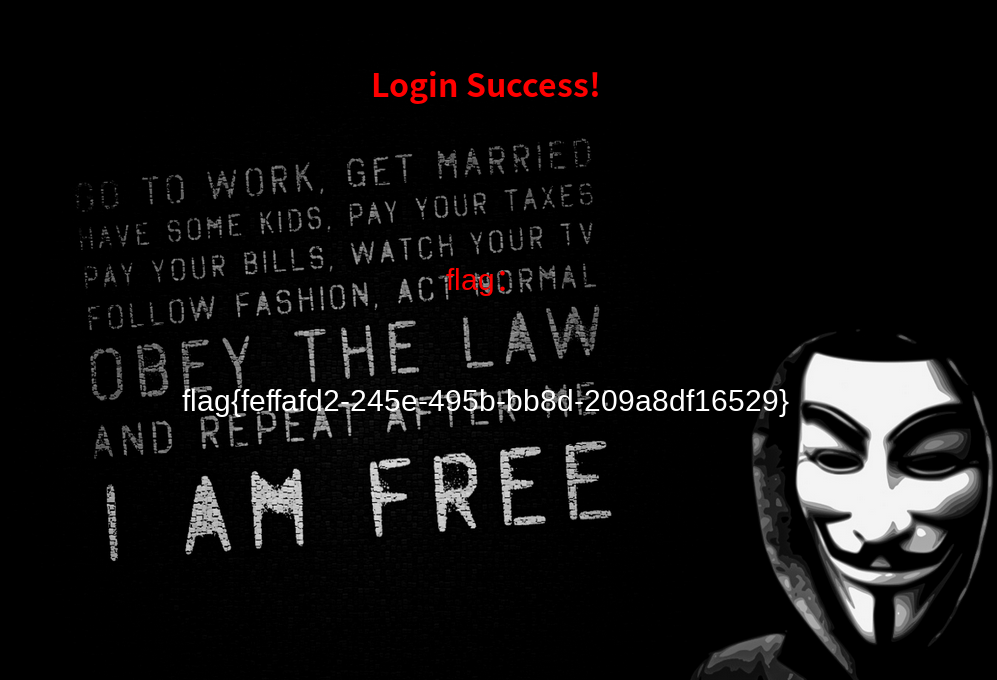
看了看别的大佬的博客
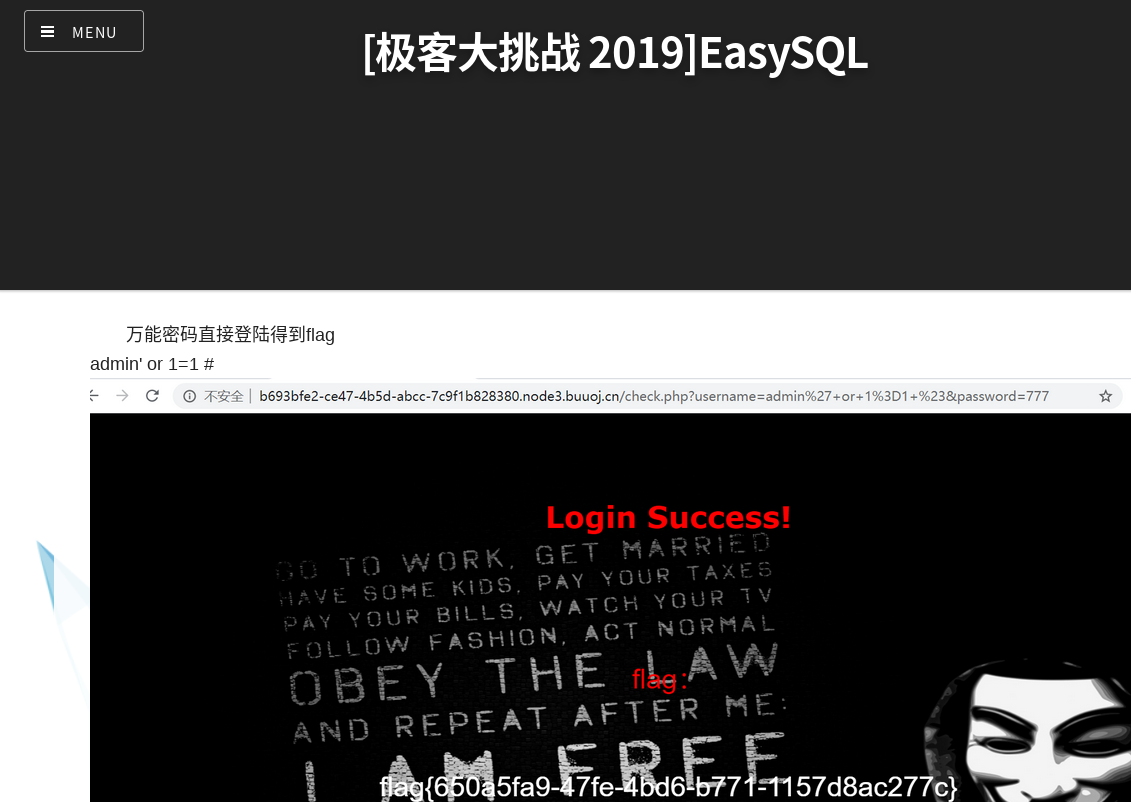
emmm,确实就这么个样。。过过过。。
Havefun
页面上什么都没有,页面源码有注释
1 | $cat=$_GET['cat']; |
输入URL/?cat=dog然后。。。flag又出来了

Secret File
源码:
1 | <html> |
直接输入flag提示看不到,尝试用filter伪协议读取
secr3t.php?file=php://filter/read=convert.base64-encode/resource=./flag.php
1 | <!DOCTYPE html> |
flag在里面
PHP
www.zip
index.php关键代码
1 |
|
class.php
1 | class Name{ |
构造饭序列化字符串,更改对象数量绕过_wakeup函数即可
exp.php
1 |
|
LoveSQL
测试admin' or '1成了,报错注入
1 | admin' order by 3# |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来源 Rick!
评论


